Dead simple encryption with sym Advantages and disadvantages of pgp encryption What is encryption? why it’s important? a brief overview
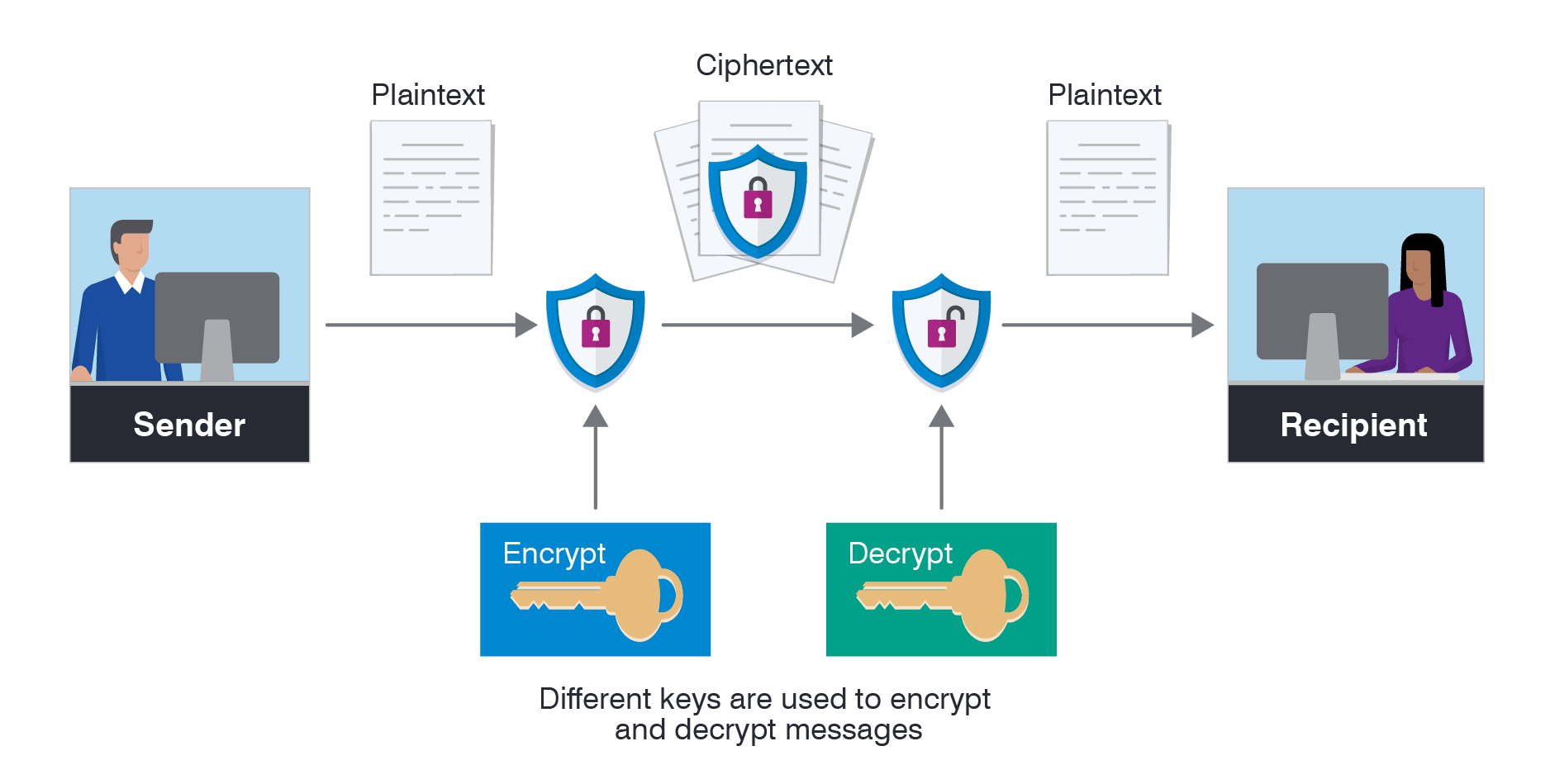
Asymmetric vs symmetric encryption graphic illustrates the asymmetric
Understanding how encryption works
Encryption key asymmetric public rsa cryptography bob secret message using users share decrypt
Encryption asymmetric does work data example works decryption use algorithms keys plaintext changesEncryption asymmetric authentication What is asymmetric encryption & how does it work?Encryption key types keys symmetric decryption diagram data cryptography figure website same ciphertext process using plaintext public ico browser consult.
Encryption asymmetric symmetric encrypt algorithms algorithm keys aes cryptography decrypt hashed definitions android thesslstore ciphertext encrypted goalEnd-to-end encryption at entperprise scale How encryption worksEncryption cyberhoot mezquita ty.

Aes encryption cryptography works advanced standard diagram key block three
Encryption email encrypted message decrypt pairsI am calvin Encryption aes decryption symmetric asymmetric cryptography cipher aws introduction commonly cryptographic encrypting programmers randomness intro ways cryptoAsymmetric vs symmetric encryption graphic illustrates the asymmetric.
Pgp encryption hashing usemynotesAes (advanced encryption standard) in cryptography Prime numbers in encryptionEncryption data numbers sender place receiver between takes prime proofpoint methods importance transfer source.